You should absolutely have patches installed in your reference image, no question about the. The default setting in Microsoft Deployment Toolkit is to run Windows Update “when needed” and the default behavior is the same, so basically Windows will run Windows Update when it “feels” for it. When the machine is managed it is controlled, but a reference image is created when the operating system is unmanaged. This could result in all kinds of issues, it could result in a pending reboot “sometimes” or failure to install software “sometimes”. I don’t like “sometimes” or random…
Turn of random Windows Updates during reference image creation
It is actually very easy, you need to change “Protect Your PC” from 1 to 3
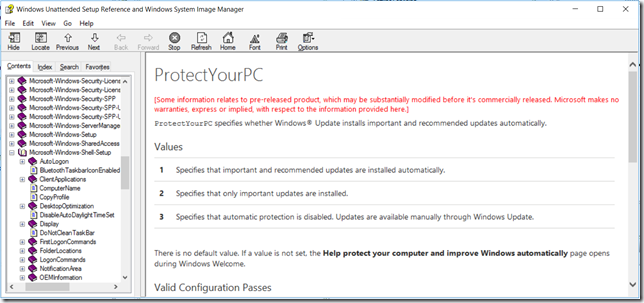
All settings for ProtectYourPC.
If you open the unattend.xml file in Windows System Image Manager it looks like this:

ProtectYourPC is now set to 3.
This way Windows Update will performed manually or since you are using MDT and LiteTouch as your tool to create the reference image, the two Windows Update steps will do the updates and no more “random” updates.

The two Windows Update steps in the LTI task sequence.
/mike
Categories: OS Deployment, OSD




Could I do something like this before the Windows Update Steps instead of modifying the unattended.xml? – reg add HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\OOBE /v ProtectYourPC /t REG_DWORD /d 1 /f
Not sure, in theory that could work, I have not tried that. The problem is that you would like this setting to effective ASAP, otherwise WU could kick in and even if it works, you most likely need to restart components to honor that setting. It works in the unattend.xml, that I know.
Yes you can. I have been doing this with great success in our environment. I think the unattend.xml approach is more elegant however. I call a PowerShell script via Run Command Line. You can use a similar script to change the setting back at the end of the TS. Ideally you would write a single script and use a parameter to turn updates off then on later:
$regkey0 = “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\”
$regkey = “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\”
$name = “NoAutoUpdate”
If (!(Get-ItemProperty $regkey0 -ErrorAction SilentlyContinue))
{ Md $regkey0 }
If (!(Get-ItemProperty $regkey -ErrorAction SilentlyContinue))
{ Md $regkey
New-ItemProperty $regkey -Name $name -Value 1 -PropertyType “DWord” }
If (!(Get-ItemProperty $regkey $name -ErrorAction SilentlyContinue))
{ New-ItemProperty $regkey -Name $name -Value 1 -PropertyType “DWord” }
Another way you can stop it by configuring these registry setting is to edit them in the WIM file so it’s disabled ‘out of the box’
There is a guide on doing this out on technet:
https://blogs.technet.microsoft.com/migreene/2006/12/07/edit-the-registry-on-a-mounted-wim/
This article is a bit confusing… you say in the text to change it from 3 to 1. Then later, you say “Protect your PC is now set to 3.” The description of ProtectYourPC leads me to believe that we would want it set to 3 if we want to resolve this issue… can you confirm and update the article?
Updated, sorry about that
I think it’s the other way, from 1 to 3
You wrote:
“It is actually very easy, you need to change “Protect Your PC” from 3 to 1”
Yes, I have updated the post, sorry
Should the setting not be changed from “1” to “3” rather than “3” to “1”?
True, the post is updated
Microsoft changed this for Windows 10. There doesn’t appear to be an equivalent setting to prevent updates. https://msdn.microsoft.com/en-us/library/windows/hardware/dn915741(v=vs.85).aspx
Yes, but 3 still turns it off for Enterprise and for the Education :
3 – Turns off Express settings.
I was randomly getting network driver updates during deployment of Windows 10 Enterprise 1511. I opened a Premier ticket, and Microsoft said the only way to prevent it is to set this registry key. HKLM\Software\Policies\Microsoft\Windows\DriverSearching
Value: SearchOrderConfig. This is set to 0 = > Do not search Windows Update
They said the ProtectMyPC didn’t prevent the update.
Thank you for the info about the registry value. I have tro try that. We’ve had lots of problem during Windows 10 Enterprise 1511 deployment. With several “failure to install software sometimes” scenarios. Turns out the damn WU tries to download and update drivers during deployment and causing lots of 1618 errors when MDT tries to install applications. And changing “Protect Your PC” from 1 to 3 did not help in those cases. Right now I just run a script to completely disable the WU service and reboot the computer before application installation, and then enable it again once it’s completed. Not ideal, but at least we don’t get 1 or 2 random application installation failures on every other computer we deploy.
I like Windows 10. But from an enterprise deployment point of view Windows 7 is far more trustworthy.
That is different, driver update is not related to that setting, it also does not relate to reference images, since they never have drivers. ProtectMyPC is for Windows Update, downloading updates and patches and is not related to drivers, since that is related to DriverSearch
If you assign a variable, like “OSDisk” to the “Windows (Primary)” partition in the “Partition Disk” steps of your task sequence, you can use a “Run Command Line” task sequence command like this one below to make the registry edit.
CMD.exe /C REG.exe LOAD HKLM\TEMP_SOFTWARE %OSDisk%\Windows\System32\Config\Software && CMD.exe /C REG.exe ADD HKLM\TEMP_SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU /V NoAutoUpdate /T REG_DWORD /D 1 /F && CMD.exe /C REG.exe UNLOAD HKLM\TEMP_SOFTWARE
Using REG.exe instead of Powershell has the benefit of not requiring the full path to the registry having to exist first.
Or if your partitioning steps ALWAY result in your OS Partition being assigned drive C: in WinPE, then just replace %OSDisk% with C:
I would assign the partition though because it helps with alot with little offline OS tweaks you can perform during the WinPE Phase like file copies and registry tweaks like this.